Secure a weak link: 3rd Party APIs
Subkeys obfuscates your 3rd Party API connections and adds least privilege principle capabilities by virtualizing your API keys.
Key Benefits
Consistent Restrictions
Apply your own restrictions consistently across any provider to match your security policies and tolerances. Examples are by endpoint, method, timeframe, IP address, and more.
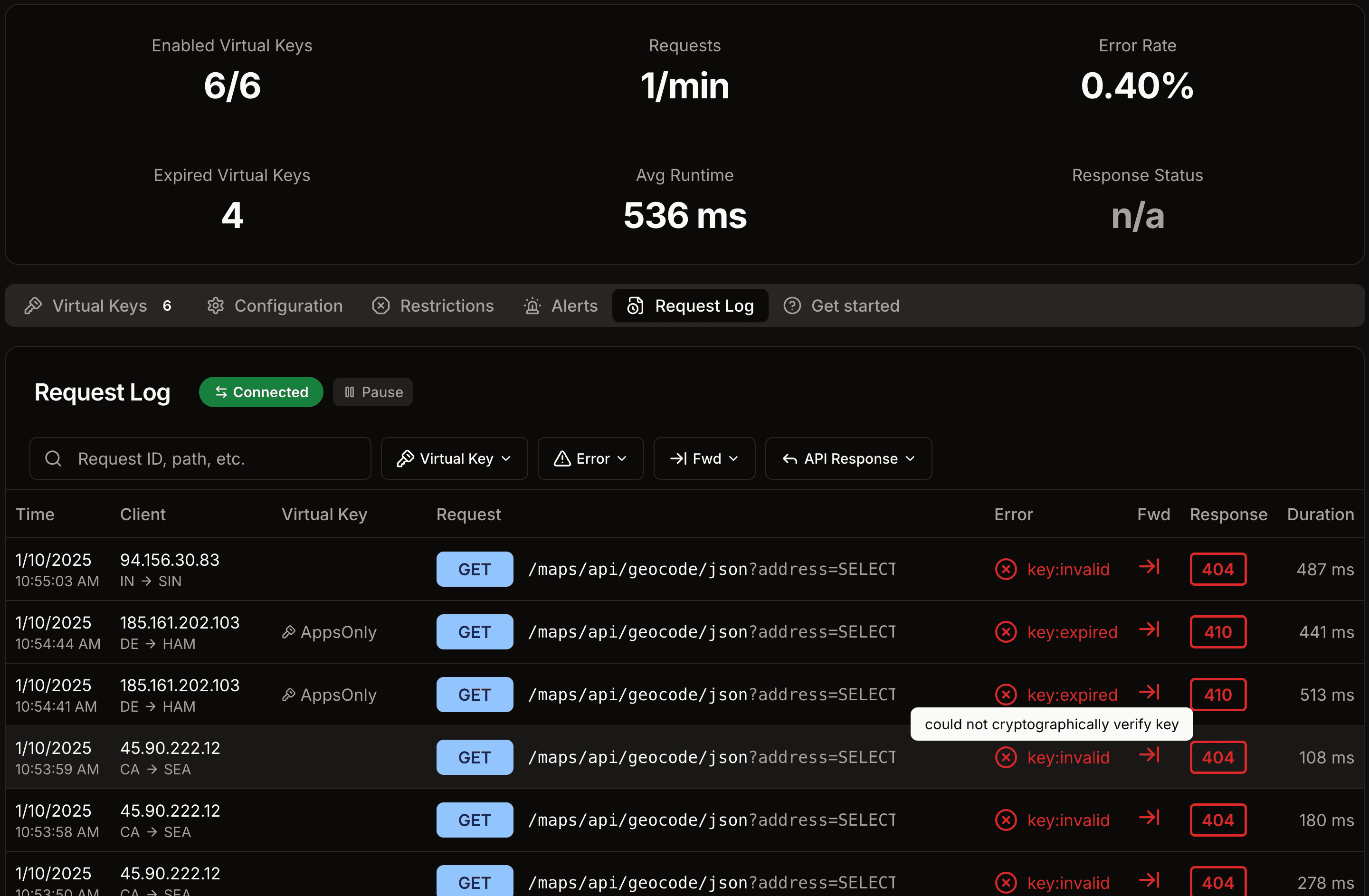
Analytics and Alerting
Gain visibility and alerting down to the most granular level. Configure smart alerts based on specific key usage and abnormal behaviors.
Auditing & Compliance
Fulfill compliance requirements and simplify auditing by applying Least Privilege Principle to your APIs. Don't just assess risk, reduce it.