Share Virtual Keys, not API Keys
Take control of your 3rd Party APIs with virtual keys
How it works
Step 1:
Create virtual keys
Step 2:
Distribute virtual keys
Step 3:
Get complete visibility
Unlock the Power of Virtual Keys
Unified visibility and control for APIs
Learn more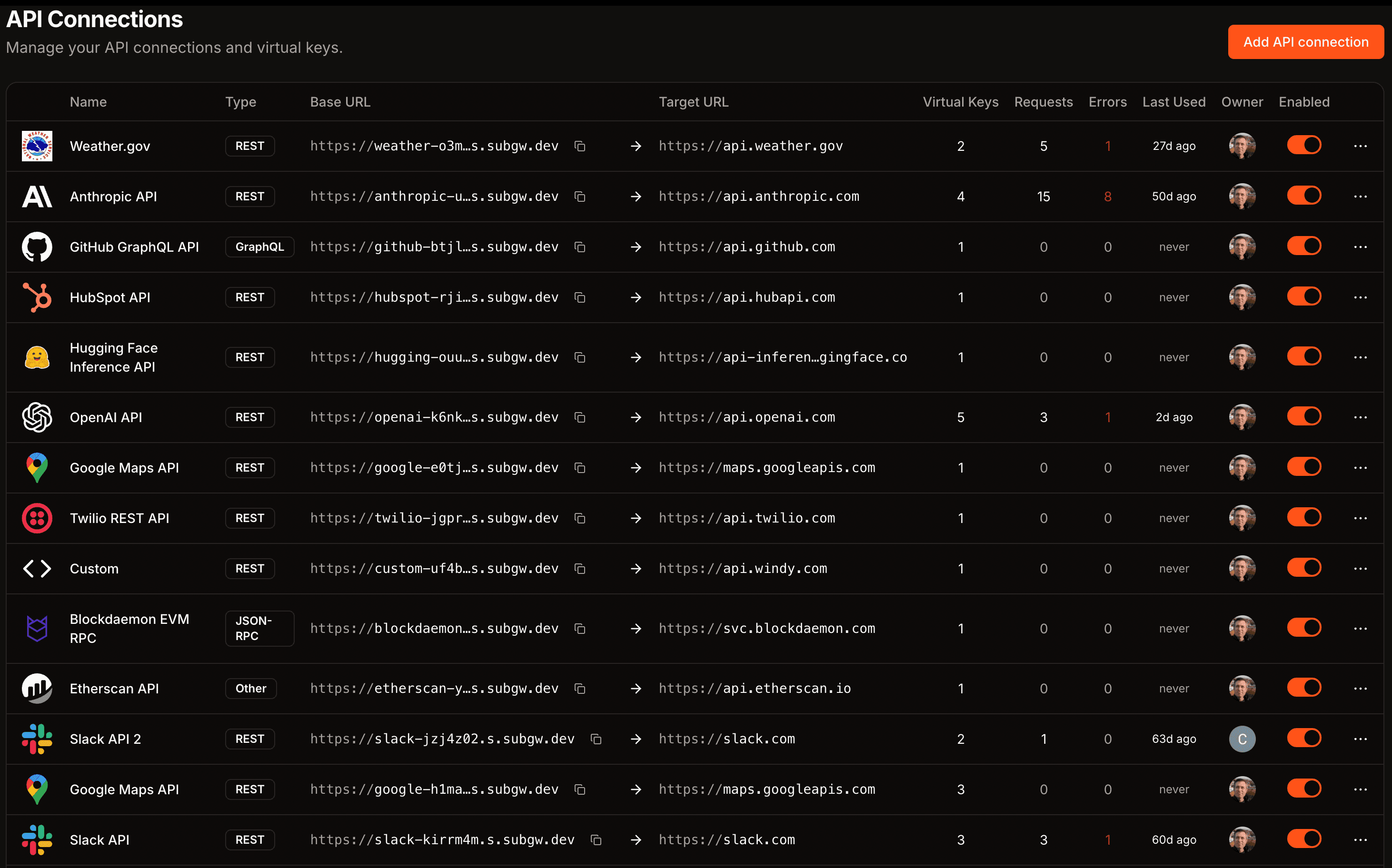
Improve security while removing friction
Learn more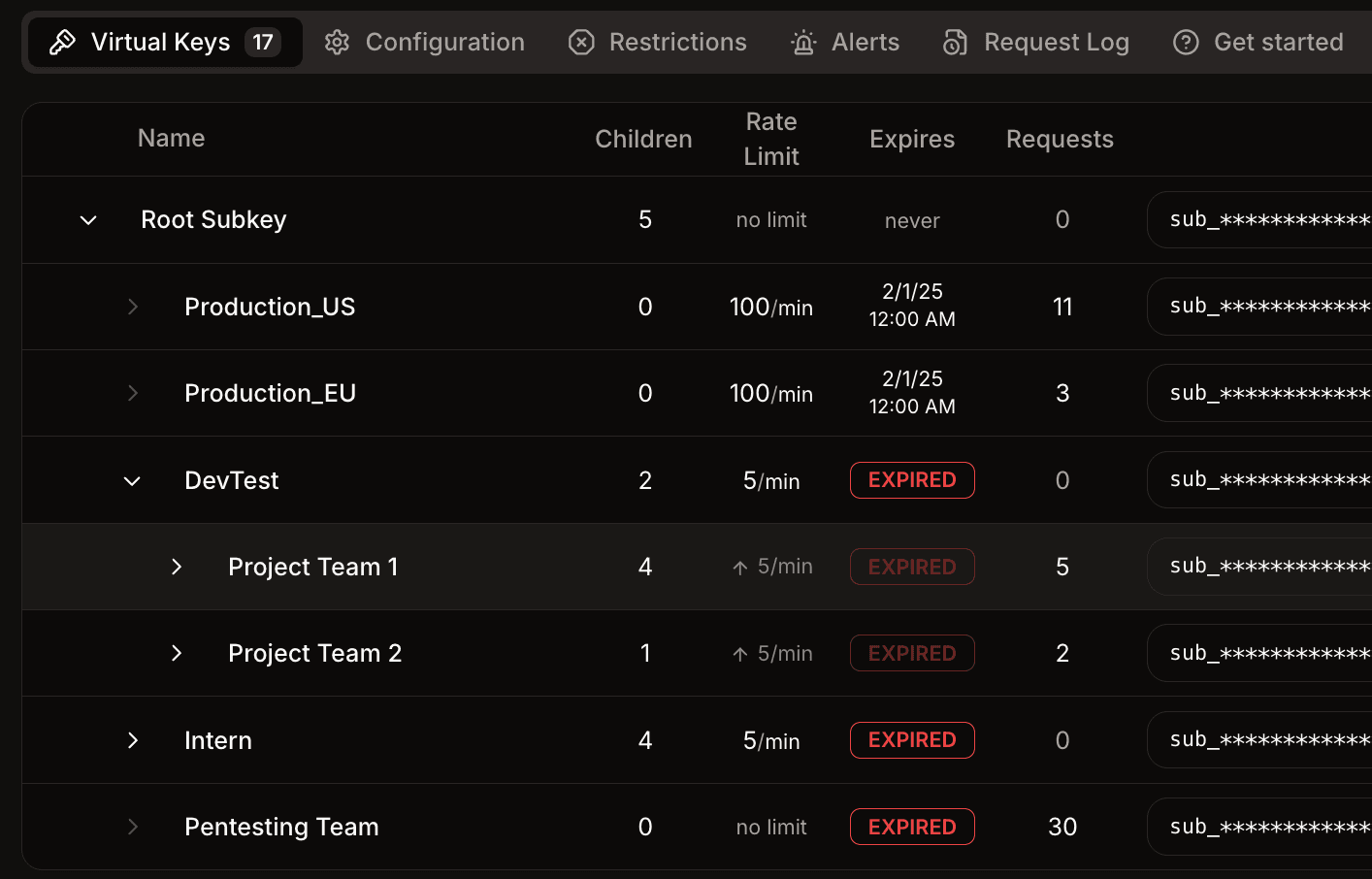
Delegate API access to vendors, partners, and customers.
Learn more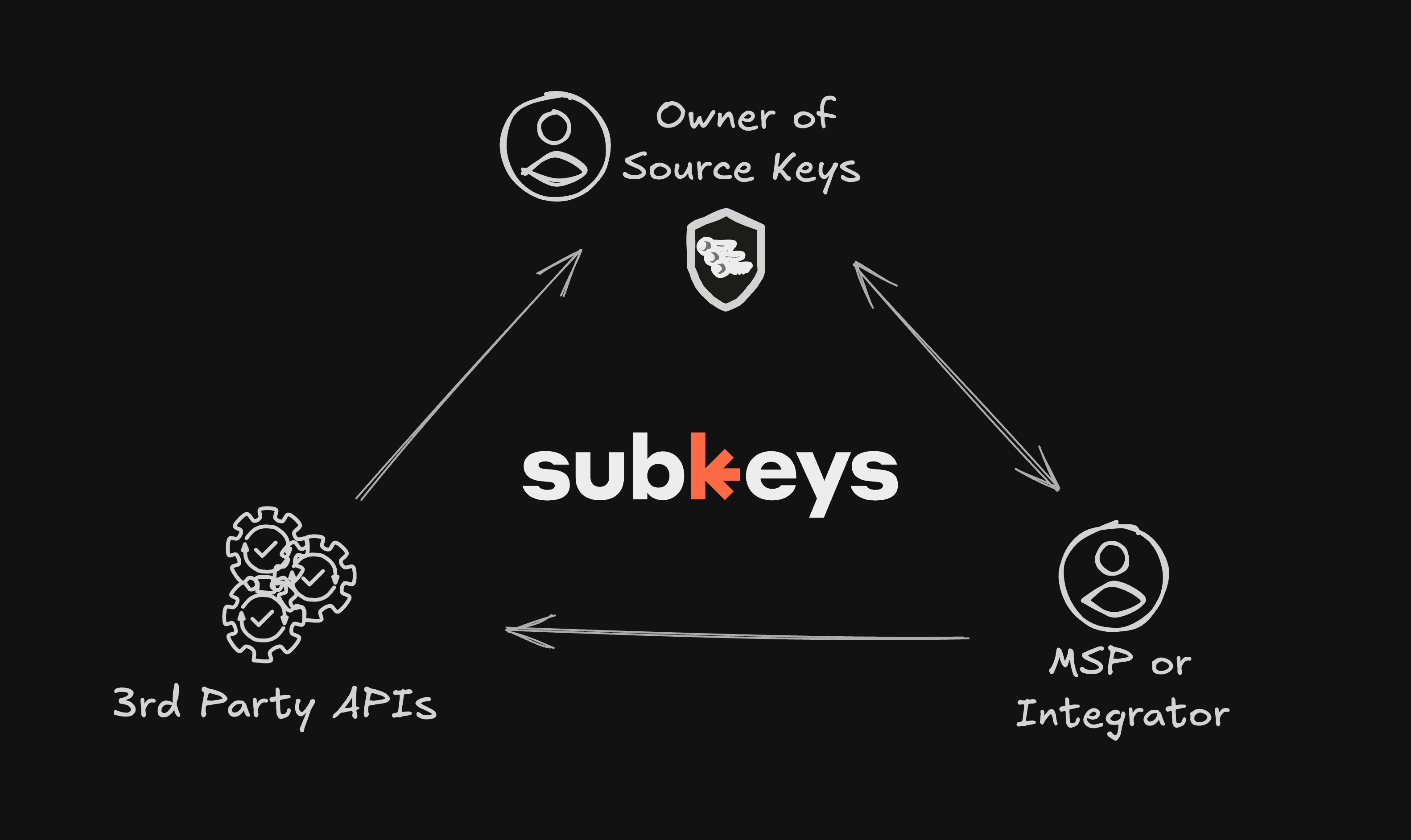
What people are saying
Cost Savings
"A coding bug led to over $100k in API overage fees over two months. Subkeys offer a safeguard against such costly errors."
Web3 Data Engineer
Improved Security
"Our developers were unaware of the financial impact of AI API calls on our company. With subkeys, overspending concerns are a thing of the past. We can share subkeys with multiple users and applications while protecting our main key."
Infrastructure lead
Time Savings
"We were apprehensive about revoking an API key due to potential impacts on critical applications. With subkeys, we could have saved six months of application analysis."
Large US exchange
Improved Trust
"Subkeys enabled us to streamline renewals, prevent service disruptions, and remove handling of sensitive credentials across stakeholders simply by letting our customers securely manager their own virtual keys."
Managed Service Provider